Simple, everyday connectivity mistakes can be more damaging than expected. More shockingly, they often go unidentified.

When meeting a prospect in the cafeteria I overheard an employee asking a colleague how to connect his new phone to the Wi-Fi and was shocked to hear the mention of inputting AD (active directory) credentials. In a company, like this, which invests significantly in security, surely these outdated mistakes should have been put to rest long ago.
When I asked this employee if he knew who he was providing his credential to it became clear that the question had never even crossed his mind. He explained to me that he was accustomed to the dialog box on his screen, having encountered it using his previous phone which had required him to update Wi-Fi client settings each time his company’s passwords were changed every three months.
There are several security risks to be aware of in this case. Let me explain why.
Network Authentication Protocols
Protocols such as PEAP (Protected Extensible Authentication Protocol) and TTLS (Tunnelled Transport Layer Security) were developed to provide enhanced security in Wi-Fi environments with minimal impact on the client (user) provisioning side, introducing username and password authentication. The principle is the following:
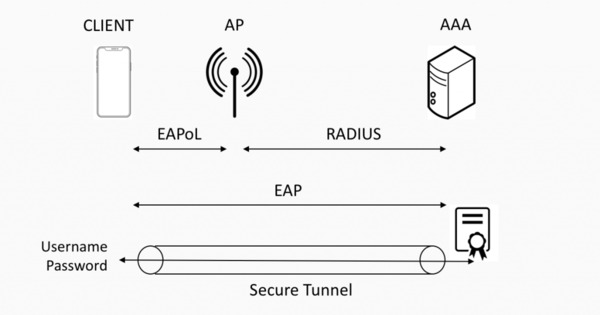
The client communicates with the authentication server by sending EAPoL (Extensible Authentication Protocol over Local Area Network) traffic to the AP that forwards it to the AAA (authentication, authorization, and accounting) server by encapsulating it into RADIUS (Remote Authentication Dial-In User Service) packets.
There are various EAP methods that specify the ‘language’ used to connect the client to the AAA server; PEAP and TTLS are just two examples of these languages. The principle is to facilitate the client to authenticate the server by verifying a digital certificate, establishing a secure tunnel with the AAA server. Once this tunnel has been established, user credentials can be sent securely.
This method has the advantage of offering secure authentication without having to deploy a certificate on each individual client, an expensive and time-consuming exercise. PEAP or TTLS were defined when mobile device management or device onboarding solutions were still in their infancy in the early 2000’s.
The issue with mechanisms of this kind is that they rely on the client side to decide which server certificate to accept. Most operating systems will allow users to select or configure preferred certificates, and some might also accept untrusted certificates providing appropriate user warnings. The user may not necessarily be familiar with the implications or the consequent risks of making the wrong decision, more often concerned with getting connected as soon as possible. If the AP (authentication protocol) and the AAA server were rogue devices, making the wrong choice could allow a malicious a person to obtain the user credentials needed to access network connectivity or any other IT system used by that company.
Secure Network Authentication with Cloudpath
Today many solutions are available to centrally automate this process and prevent human error from causing potential security risks. While some are OS specific such as Apple Mobile Configurator or Microsoft Group Policy Manager there are others available which support a wide variety of operating systems such as Cloudpath Enrollment System or other Mobile Device Management solutions. Additionally, some of those solutions can create a device certificate on the fly and install them on the user equipment immediately. This allows certificate authentication to be achieved on the mobile device as well as previously connected equipment without the need for user credentials, allowing the network to identify the device and not just its user.
A centrally automated process could allow IT departments to implement different network access policies based on the device being used (accommodating both personal mobile devices and company-owned laptops). Not only does this type of differentiation achieve more convenient data access controls for the user, it significantly reduces the risk of data breaches in Wi-Fi security.
Continued reading:
New e-book links poor network access security to data breach risk
Eastern Europe bank hack highlights the need for network access security