Aurora Networks® (ANS) and RUCKUS® Networks are now Vistance Networks
As we say good riddance to 2020, a year which some say was “the worst year in cybersecurity history,” we say hello to 2021 – with its continued work from home restrictions and the requirement to formalize mitigation strategies regarding agencies’ use of compromised monitoring software. CommScope understands the challenges our government clients face, and we have compiled this list of top network security trends to expect for 2021. Some items listed below are new solutions to old problems (#2 and 3), some are old solutions to new problems (#4), and there may even be a couple new solutions to new problems (#1 and 5).
#5 The Rise of Wi-Fi 6

While the Wi-Fi 6 (or 802.11AX) certification was finalized by the Wi-Fi Alliance in September 2019, this compelling technology is currently seeing a surge in growth as users start to demand higher throughput, longer battery life, and increased capacity. In Q3 2020, worldwide smartphone sales approached 367 million units sold—most of which are now Wi-Fi 6 capable. Although Wi-Fi 6 is markedly more efficient, there are three key security trends associated with the growth of these new devices:
- Starting with Apple IOS 14 and Android 10, a reckless attempt was made by the consumer product manufacturers to outsource end-user security to the end-user with a feature called Private Addressing that is enabled by default. MAC Randomization, as it is also called, causes issues with DHCP server pool exhaustion, MACauth, and user blocking that is based on MAC addresses. In 2021, DHCP server lease times will need to be shortened to avoid network availability issues. You will likely also start to see more analytics tools from Wi-Fi vendors indicating false positives of rogue clients caused by MAC Randomization. Additionally, this year will see a concerted effort by Wi-Fi vendors to encourage utilizing more “user-based identification” methods such as Dynamic PSK, eDPSK, Identity PSK, and Private PSK.
- Wi-Fi Protected Access 3 (WPA3) was not necessarily built for Wi-Fi 6, but all the devices connecting over an 802.11AX network will have WPA3 compatibility. Although WPA3-Enteprise does not offer many advantages over its WPA2 predecessor, federal agencies are able to utilize 192-bit cryptography built into the new technology. This provides a more secure form of encryption (than 128-bit) and gives enterprise networks better resiliency than WPA2. (Note that WPA 3.1 addresses the Dragonblood exploit).
- Because 802.11AX’s higher throughput rates present downstream bandwidth and latency challenges – in addition to the authentication complexity issues – 2021 will have admins requesting more advanced network monitoring troubleshooting tools. You will start to see vendors working harder to lock-in customers to all-in-one management suites and AI-driven analytics These tools will allow a holistic view of an agency’s wireless and wired network and are robust alternatives to third-party network monitoring software.
#4 WFH Security – Providing Alternatives to Traditional VPNs
No list of 2021 predictions would be complete without security analysts noting the potential difficulties agencies will have continuing to support a remote workforce. Agencies have experienced VPN vulnerabilities caused by user tampering and poor configurations, as well as other issues with segmentation, scaling, and setting-up multicast. 2021 will see networking vendors push their VPN alternatives including SD-WAN and/or encrypted GRE tunneling options to provide comprehensive solutions that may mitigate VPN security challenges.
With the Pentagon recently relaxing regulations allowing DoD civilians to telework, federal agencies will require solutions which provide split-tunneling options for some user accounts and disabled split-tunneling for other accounts. Moreover, there will be requirements for employees to update their ill-protected home gateway routers that have poor QoS and low bandwidth, creating challenging latency issues on team calls. Simultaneously, federal employees will be requesting gateway upgrades that provide better coverage for their wired and wireless devices as well as an easier experience accessing internal files – so that logging on at-home is as seamless as what they experience in the office. Finally, despite funds being allocated for VPN connectivity solutions, procurement offices will be looking for alternative fixed-pricing options that are cost-effective and scale to their agency’s needs rather than relying on expensive and complicated subscription services.
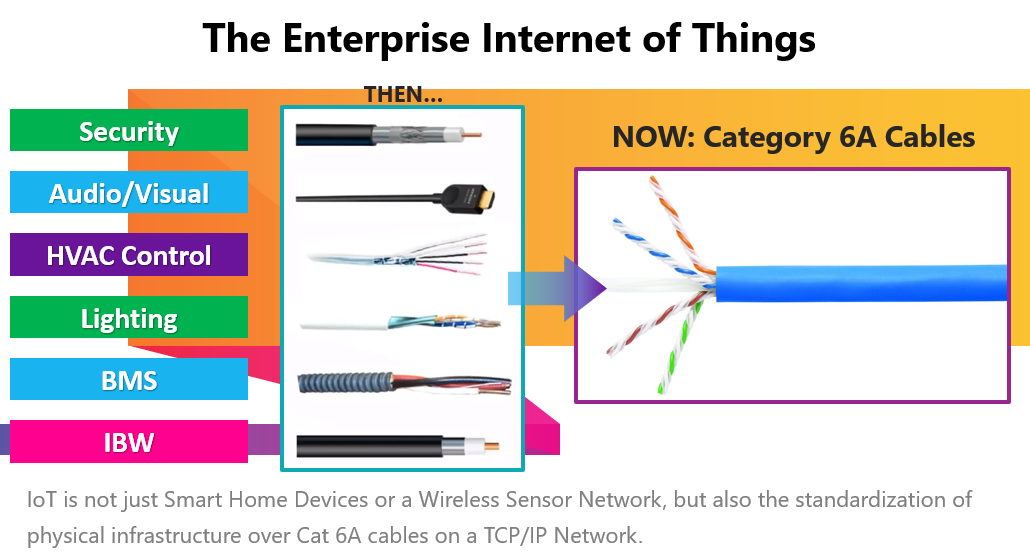
#3 Securing Headless Devices
The Internet of Things (IoT) is an ambiguous term most closely associated with either smart home devices or a Wireless Sensor Network; however, in the same way that most smartphone companies standardized on USB-C, most infrastructure equipment is now moving to Cat 6A cabling over TCP/IP. These “things” which had not traditionally been Internet-connected, are notable for having low data flows and high PoE budgets, while not utilizing FIPS-validated encryption.
This will continue to be an important trend as agencies upgrade systems to include these additional IoT devices. Proper planning will have to include more than just PoE budgets and IP schemes. Agencies must be aware of the new risks associated with headless devices including DDoS, sniffing, and vectoring attacks. Agencies will look for technologies capable of securing headless devices by dynamically assigning pre-configured VLANs and appropriate ACLs to effectively segment and safeguard all IoT devices – both wired and wireless.
This topic is also of interest to us this year because of H.R. 1668 becoming a law on December 4, 2020, requiring NIST “to develop and publish standards and guidelines for the federal government on the appropriate use and management by agencies of IoT devices” by mid-year 2021 (see more here: https://www.congress.gov/bill/116th-congress/house-bill/1668).
#2 New forms of Wireless Communications
While Wi-Fi 6 receives a great deal of attention, it is important to note that Private LTE, or CBRS – which utilizes the 3.55-3.70 GHz spectrum – is a favorite of many agencies who require a more secure form of on-site wireless connectivity. Projections indicate that up to 90% of smartphones will be CBRS compatible by 2023; correspondingly, vendors of CBRS access points (called CBSDs) will start to position the technology in certain environments as an alternative to Wi-Fi in 2021. Along with the security advantages of LTE, CBRS requires that devices be “lightly licensed” and that the Spectrum Access System (SAS) monitors spectrum to ensure there is no harmful interference. These requirements reduce the security risks associated with unlicensed spectrum (Wi-Fi) such as Evil Twin Attacks, Man-in-the-Middle Attacks, Rogue APs, Rogue Clients, and Wardriving. CBRS can be seen as Wi-Fi managed like LTE, or as LTE at the price point of a Wi-Fi network, and will give agencies a reliable QoS path with minimal interference for critical applications.
#1 Zero Trust Architecture Implementations
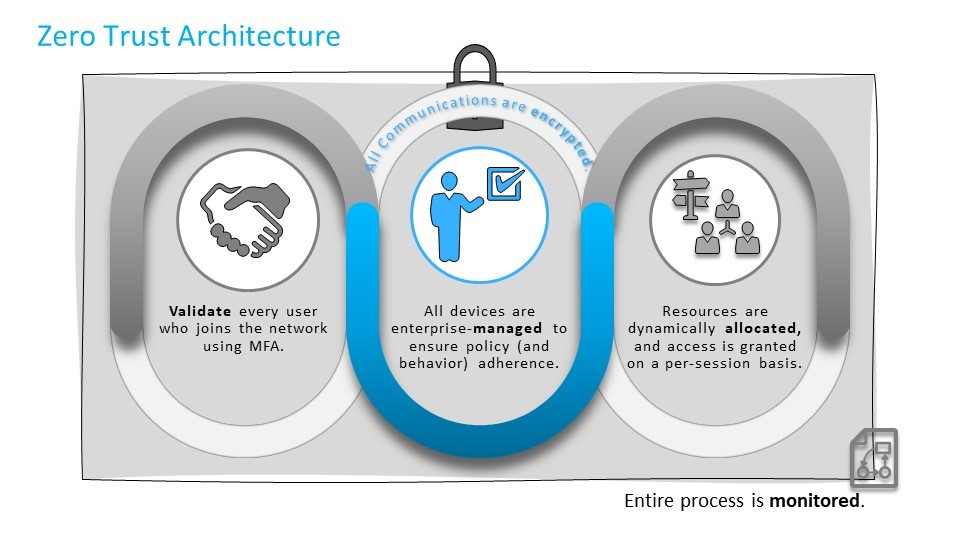
Before the term Zero Trust Architecture (ZTA) gets hijacked to refer to a specific company or product, it’s important for network engineers to understand that ZTA is a NIST-defined strategy, oftentimes involving multiple interconnected system components. Fundamentally, ZTA necessitates that every network connection be verified and validated properly and access to resources is dynamic and granted on a per-session basis. In a ZTA, all users and all actions are treated as malicious. In 2021 and beyond, it will be important to ask how vendors help your agency network accomplish a ZTA, including:
- Do you employ MFA?
- Are you using FIPS-validated encryption for data-in-motion (or at-rest)?
- To what level of granularity do you…
- ensure devices adhere to policies?
- grant access based on user identities?
- track user movement?
- inspect and log meta data associated with encrypted traffic?
- Can you interoperate with my current infrastructure?
- How will your solution scale over the next five years?
CommScope will be publishing a White Paper and Best Practice Design Guide on ZTA later this year, so stay tuned!
Have you experienced challenges implementing your Work-From-Home solution? Or are you interested in learning about how RUCKUS fits into your 2021 Zero Trust objectives? If so, please contact your CommScope sales representative today.